Rainbow authentication portal (1.243.1)
Download OpenAPI specification:Download
Introduction
This guide describes list of API services that are provided by OT Rainbow authentication portal system. Services are used to manage OT Rainbow authentication.
Protocol
REST interface is used for sending/receiving OT rainbow API messages.
HTTP request GET is used. Standard HTTP responses are used to provide requested information or error status. There is no session notion in OT Rainbow system, so requests could be issued according stateless model, without transport conservation between them.
JSON is used as a main format for data encoding in message body part. Each request is started with the following pattern /{module}/{version}/ where {module} is a portal module name to address and {version} is a version of used API, par example, “v1.0”.
Security considerations
Each request should contain some credential information to authenticate itself. Standard HTTP authentication with basic/bearer modes is used. JSON Web Token mechanism is used to provide authentication information. JWT has a expire timeout that is controlled by OT Rainbow portal to prevent very long token usage. Also authentication with application token is used. The token must be provided in the request HTTP header, using a custom header: APIKey. At server side, token is verified, and if it doesn’t match, 403 Not Allowed response is sent. TLS is used as a transport protocol to support message exchanges between OT Rainbow portal and an application.
Bearer
For accessing the API, a valid JWT token or a valid OAuth access token can be passed in the 'Authorization' header.
- JWT
- A valid JWT token is obtained from authentication APIs, depending on the user configuration (given by the API GET /api/rainbow/authentication/v1.0/urls):
- Rainbow password authentication, using API GET /api/rainbow/authentication/v1.0/login
- Rainbow password authentication with Multi-Factor Authentication, using API POST /api/rainbow/authentication/v1.0/mfa/totp/login
- Rainbow passwordless authentication, using API POST /api/rainbow/authentication/v1.0/passwordless/login
- SAML SingleSignOn authentication, using API GET /api/rainbow/authentication/v1.0/saml/login
- OIDC SingleSignOn authentication, using API GET /api/rainbow/authentication/v1.0/oidc-client/login
- The following syntax must be used in the 'Authorization' header:
Bearer xxxxxx.yyyyyyy.zzzzzz
- A valid JWT token is obtained from authentication APIs, depending on the user configuration (given by the API GET /api/rainbow/authentication/v1.0/urls):
- OAuth access token
- A valid OAuth access token is generated and returned as answer of the OAuth 2.0 workflow with authorization code grant. This is done by calling the route GET /api/rainbow/authentication/v1.0/oauth/authorize to get an authorization code and then POST /api/rainbow/authentication/v1.0/oauth/token to exchange it against an access_token and a refresh_token.
- The following syntax must be used in the 'Authorization' header:
Bearer xxxxxx.yyyyyyy.zzzzzz
| Security Scheme Type | API Key |
|---|---|
| Header parameter name: | Authorization |
Bearer-x-rainbow-api-key
For accessing the API, a valid API Key can be provided instead of 'Authorization' Bearer JWT header
This authentication method is useful for some applications needing a permanent authentication or not able to expose an interface allowing the user to authenticate (scripts, bots, IOT devices, ...).
A valid API Key is obtained from the API POST /api/rainbow/authentication/v1.0/apikeys.
When API Key authentication is used, the header x-rainbow-app-auth is mandatory to authenticate the application accessing the API.
| Security Scheme Type | API Key |
|---|---|
| Header parameter name: | x-rainbow-api-key |
Bearer-x-rainbow-challenge
Challenge for application authentication.
Should be randomly generated by the application (the challenge should be unique for each request for security reasons).
Mandatory only for authentication with x-rainbow-api-key (not used for authentication with JWT).
| Security Scheme Type | String |
|---|
Bearer-x-rainbow-app-auth
Application authentication
Basic <base64encode(appId:sha256(appSecret challenge))> (Concatenation of appSecret and provided challenge, hashed with sha256).
The challenge used to compute the x-rainbow-app-auth value must be the same as the one provided in header x-rainbow-challenge.
Mandatory only for authentication with x-rainbow-api-key (not used for authentication with JWT).
| Security Scheme Type | String |
|---|
Get user authentication URLs
This API allows Rainbow users to know that URL they can use to perform a login.
The authentication URLs depends on the user and/or his company's setting:
- user can be configured to use:
- Rainbow passwordless authentication
- Rainbow password + MFA authentication
- Rainbow password authentication
- Single Sign On (SSO) authentication (OIDC, SAML, global SSO method when available)
- Company's default authentication method
- When the user is not configured to use a specific authentication method, the company can be configured so its users use a given authentication method:
- Rainbow passwordless authentication
- Rainbow password + MFA authentication
- Single Sign On (SSO) authentication (OIDC, SAML, global SSO method when available)
If no authentication method is configured on the user nor on its company, Rainbow password authentication method is used.
Rainbow passwordless authentication requires the user to have the feature SECURITY_PASSWORDLESS in his profile. If that is not the case,
Rainbow password authentication method is used even if the user is configured to use passwordless authentication.
Some advanced user/device authentication performed by some SSO servers (Microsoft's conditional access, FIDO, Yubikey...) are not
correctly handled by Rainbow Desktop application (Electron based). In order to bye-pass these limitations, company's SSO settings can be configured
to be performed in user's browser instead of inside the Desktop client. This remote authentication mechanism is named backchannel in this documentation.
To be noted that whatever the authentication configuration, admin users always have the Rainbow password authentication method returned (fallback in case of authentication configuration issues).
query Parameters
| uid required | string User unique identifier:
|
| country | string When the provided
Note that an error 400210 is returned in case the provided |
| uiLocales | string {0..255}] User preferred languages When the user is configured to use an OIDC authentication type, and when supported by the OIDC provider, It is up to the client to set this value (either by using browser's language preference or by asking the user). As stated by OIDC RFC: Note that the |
| useBackchannelPolling | boolean Specifies that backchannel polling mechanism has to be initiated. When
|
header Parameters
| accept required | string application/json |
Responses
Response samples
- 200
- 400
- 500
{- "data": [
- {
- "onlyUseImplicitFlow": false,
- "clientId": "4aca5ee9a087fb9218bfb662fe92605c",
- "type": "OIDC",
- "name": "My OIDC server",
- "challenge": "dxV3ljthR6NZwHxH9ubfUkrc04xkGanAZT",
- "useBackchannel": true,
- "backchannelSession": {
- "id": "541b2028-83f8-4935-b71a-882e144dc005",
- "token": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE3MzA5OTYzNjMsImV4cCI6MTczMTAzMjM2MywiYXVkIjoiNjZkYjE0ZjRjYjlmMWQ3ZmQ0MjY1OWI3IiwianRpIjoiNTQxYjIwMjgtODNmOC00OTM1LWI3MWEtODgyZTE0NGRjMDA1In0.rA1HtiLJQ-XxgVF2goLQHxoQxj3XrnmykKN8-wljTeU"
}
}
]
}Login user
This API allows Rainbow users to login.
The application is also authenticated during the user login.
If login is successful and multi-factor authentication isn't activated for user (or activated but not configured), the API returns a JSON Web Token (<abbr title="JSON Web Token">JWT) which has to be provided by clients for all Rainbow APIs requiring user authentication:
- The JWT is valid only for a given time period.
- The JWT can be renewed a few times using API GET /api/rainbow/authentication/v1.0/renew.
- The maximum number of renew is given in the JWT payload, as well as the current number of time the token has been renewed (see below).
- Once the JWT expired, or if the maximum of token renew has been reached, user must login again using this API.
The JWT returned contains the following data in payload:
{
"countRenewed": 0, // Number of times the token has been renewed
"maxTokenRenew": 5, // Number of times the token can be renewed
"user": {
"id": "572756967bfbca0d0e09a6b4", // Logged in user id
"loginEmail": "user@company.com" // Logged in user loginEmail
},
"app": {
"id": "598983029db9b5b14693a6f0", // Application id used for the authentication
"name": "My App" // Application name
},
"iat": 1463588327, // (Issued At) Time at which the JWT was issued
"exp": 2183588327 // (Expiration Time) Expiration time after which the JWT won't be accepted
}
If the login / password combination is wrong, an error 401 is return (errorDetailsCode 401500).
If the appId / appSecret combination is wrong, an error 401 is return (errorDetailsCode 401500).
The following login protection is implemented:
- After a given number of login failure (5 by default), the user account is locked for a given time period (60 min by default).
- As long as the maximum number of login failure has not been reached, a 401 error with errorDetailsCode
401500is returned. - Once the maximum number of login attempts has been reached, a 401 error with errorDetailsCode
401501is returned: the user account is locked for the given time period. - While the user account is locked, the same response with errorDetailsCode
401501will be returned for each new login attempt for this user account (even if a good login / password combination is provided). If the login / password combination is wrong, the locked time period restarts from this new wrong attempt. - Once the locked time period is over, a login with the good credentials will be allowed.
- While the account is locked, the user can reset his password. In that case, his account will be unlocked and he will be able to login with his new password.
- While the account is locked, a superadmin / support / admin (organisation or company level) user can set a new password for this account. In that case, this account will be unlocked and the user will be able to login with this new password.
If multi-factor authentication is activated for the user and enabled, depending on the configuration of selected policy the API may return a JSON Web Token (<abbr title="JSON Web Token">JWT) which has to be provided by clients for all Rainbow MFA APIs requiring user authentication:
- The JWT is valid only for a short given time period.
- The JWT can't be renewed.
- Once the JWT expired, user must login again using this API.
The JWT returned contains the following data in payload:
{
"maxTokenRenew": 0, // Number of times the token can be renewed
"user": {
"id": "572756967bfbca0d0e09a6b4", // Logged in user id
"loginEmail": "user@company.com" // Logged in user loginEmail
},
"app": {
"id": "598983029db9b5b14693a6f0", // Application id used for the authentication
"name": "My App" // Application name
},
"mfaType": "totp",
"iat": 1463588327, // (Issued At) Time at which the JWT was issued
"exp": 2183588327 // (Expiration Time) Expiration time after which the JWT won't be accepted
}
Warning
- login url is case sensitive (lowercase). For example, /Login or /LOGIN won't work.
- login will be forbidden for a certain delay if too much consecutive wrong password errors occurs, after this user has to request a password change or just wait (see implementation details above).
Authorizations:
header Parameters
| x-rainbow-app-auth required | string Application authentication Basic <base64encode( |
| x-rainbow-client-version | string The client version The client version is used to verify if the client application has the minimal version required to use the Rainbow servers infrastructure. If the version of the client is under the configured minimal version, the login is refused and an error 403 is returned (403020). The minimal version required is set by the Rainbow infrastructure team when needed (for example, when some breaking changes has been added on server side, when a security issue has been identified on client side, ...). Client version example: 1.75.0 |
| x-rainbow-trusted-appid | string an id associated to the application which realizes the login operation This id will be checked to the ones stored in datababase in case of multifactor authentication is activated for the user and configured to be run only for only unstrusted application |
| accept required | string application/json |
Responses
Response samples
- 401
- 403
- 500
{- "errorCode": 401,
- "errorMsg": "Unauthorized",
- "errorDetails": "User 5c00f9bdcf5d6c01cc8ff4b5 has a Voice Phone license. He is not authorized to log in to Rainbow.",
- "errorDetailsCode": 401223
}Logout user
This API allows Rainbow users to logout.
Note: This API must not be called with ApiKey as authentication method.
Authorizations:
header Parameters
| accept required | string application/json |
Responses
Response samples
- 200
- 401
- 403
- 500
{- "status": "User user1@company.com successfully logged out",
- "data": [ ]
}Renew user JWT
This API allows Rainbow users to renew their JSON Web Token (<abbr title="JSON Web Token">JWT), thus extending the expiration date of their current JWT.
This API requires user to be authenticated with a valid non expired JWT.
If so, a new JWT is returned, with the expiration date starting from now.
Warning:
- The JWT can only be renewed a given number of times, after this user has to login again to get a new token using API GET /api/rainbow/authentication/v1.0/login.
- The maximum number of renew is given in the JWT, as well as the current number of time the token has been renewed.
- This API must not be called with ApiKey as authentication method.
Authorizations:
header Parameters
| x-rainbow-client-version | string The client version The client version is used to verify if the client application has the minimal version required to use the Rainbow servers infrastructure. If the version of the client is under the configured minimal version, the JWT renew is refused and an error 403 is returned (403020). The minimal version required is set by the Rainbow infrastructure team when needed (for example, when some breaking changes has been added on server side, when a security issue has been identified on client side, ...). Client version example: 1.75.0 |
| accept required | string application/json |
Responses
Response samples
- 200
- 401
- 403
- 500
{- "token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1c2VyIjp7ImlkIjoiNTZjNWMxOWY5NDE0MTc2NTExOWY4OTZjIiwibG9naW5FbWFpbCI6InVzZXIxQGNvbXBhbnkuY29tIn0sImlhdCI6MTQ1NjE1MTYzOCwiZXhwIjoxNDU2MTU4ODM4fQ.FlPLNcWY9pTr0QvMj3RpLZJxtqbbydNnWIEr-B2lc4Y6ea41bqJJ-e10Sk_S-1blnG71E7yT625qrkO-UCc0ywR6lWCylcAUkH7-fvjKQbET2mU-4yuNwTd-sNHGzGabgr4n5xtUSMaDunjDgF1kQDZ-dEFPF5NtbN1rdqZP9tzTXrpZ6rmrW2a1o13-hHl7sxN_FqHr_4u_8AhN4dMKUgG0qRjrc1GMJ88M8idH9zTsejU5YQyJqdYQS9T_fSoFzJtS0rmwNCJMdeF2tXj8YQeTjKAiPXoBwklm5xblHxWeCTz9tqfkw1XeNxSO0pOUmpwdpF8kbwDCCa2rgz1z3A",
- "mfaRequired": false,
- "loggedInUser": {
- "id": "56c5c19f94141765119f896c",
- "loginEmail": "user1@company.com",
- "loginPhone": {
- "isValidated": true,
- "E164": "+33312345678",
- "national": "0312345678",
- "nationalWithoutPrefix": "312345678",
- "E164WithoutPrefix": "33312345678",
- "E164WithNationalPrefix": "+330312345678",
- "E164WithNationalPrefixWithoutPrefix": "330312345678"
}, - "firstName": "Firstname",
- "lastName": "Lastname",
- "displayName": "Firstname Lastname",
- "nickName": "Nickname",
- "title": "Mr.",
- "jobTitle": "Research and Development",
- "emails": [
- {
- "email": "user1@company.com",
- "type": "work"
}, - {
- "email": "user1@home.com",
- "type": "home"
}
], - "phoneNumbers": [
- {
- "shortNumber": "1002",
- "pbxId": "PBX712e-bd96-0c27-4350-a3ff-dc0c-83e7-c246",
- "systemId": "57dc0644f44a97c9155cd462",
- "country": "FRA",
- "number": "0390676767",
- "numberE164": "+33390676767",
- "phoneNumberId": "58876dad81e063e01187dd24",
- "isMonitored": true,
- "isFromSystem": true,
- "deviceType": "landline",
- "type": "work"
}, - {
- "number": "0390909090",
- "country": "FRA",
- "numberE164": "+33390909090",
- "phoneNumberId": "577e2e9b86c953de7838d635",
- "systemId": null,
- "isFromSystem": false,
- "deviceType": "landline",
- "type": "home"
}, - {
- "number": "0690909090",
- "country": "FRA",
- "numberE164": "+33690909090",
- "phoneNumberId": "577e2e9b86c953de7838d636",
- "systemId": null,
- "isFromSystem": false,
- "deviceType": "mobile",
- "type": "home"
}
], - "country": "FRA",
- "language": "fr-FR",
- "timezone": "Europe/Paris",
- "jid_im": "2d2f1aaf5ce54a2dbae9d70490366562@openrainbow.com",
- "jid_tel": "tel_2d2f1aaf5ce54a2dbae9d70490366562@openrainbow.com",
- "jid_password": "3b3f6e2c927940b2875f1ec604c0363b",
- "roles": [
- "user",
- "superadmin"
], - "adminType": "undefined",
- "companyId": "569ce8c8f9336c471b98eda1",
- "companyName": "My company",
- "isInDefaultCompany": false,
- "organisationId": null,
- "siteId": null,
- "visibility": "same_than_company",
- "isActive": true,
- "isInitialized": true,
- "initializationDate": "2016-01-18T13:30:44.498Z",
- "activationDate": "2016-01-18T13:29:44.498Z",
- "creationDate": "2016-01-18T12:45:44.498Z",
- "lastUpdateDate": "2016-01-19T16:33:22.548Z",
- "lastAvatarUpdateDate": "2016-01-19T11:29:11.567Z",
- "createdBySelfRegister": true,
- "createdByAdmin": {
- "userId": "56d69d020c92b35b3041d433",
- "loginEmail": "superadmin@localhost.fr"
}, - "invitedBy": {
- "invitationId": "574ffe07170a86f3297bc35b",
- "invitationDate": "2016-01-15T13:29:44.498Z",
- "userId": "56d69d020c92b35b3041d533",
- "loginEmail": "user0@company.com"
}, - "firstLoginDate": "2016-01-18T13:29:44.498Z",
- "lastLoginDate": "2016-02-23T09:17:42.523Z",
- "loggedSince": "2016-02-23T09:17:42.523Z",
- "isTerminated": false,
- "guestMode": false,
- "profiles": [
- {
- "isDefault": true,
- "status": "active",
- "canBeSold": false,
- "businessModel": "none",
- "businessSpecific": [
- "NONE"
], - "isExclusive": false,
- "isPrepaid": false,
- "hasConference": false,
- "isBundle": false,
- "assignationDate": "2017-02-17T13:35:27.427Z",
- "provisioningNeeded": [ ],
- "subscriptionId": "5808da2e35d795966e61f9ce",
- "offerId": "58079ed2041fa586e92337cd",
- "offerName": "Essential",
- "profileId": "580777f56fbd22a442d4fb57",
- "profileName": "Essential",
- "offerReference": "RB-Essential",
- "offerDescription": "Rainbow Essential offer",
- "offerTechnicalDescription": "Essential"
}
], - "customData": {
- "key1ANumber": 123,
- "key2AString": "a string",
- "key3ABoolean": true,
- "key4AnObject": {
- "myKey": "My value"
}
}, - "fileSharingCustomisation": "enabled",
- "userTitleNameCustomisation": "enabled",
- "softphoneOnlyCustomisation": "disabled",
- "useRoomCustomisation": "enabled",
- "phoneMeetingCustomisation": "enabled",
- "useChannelCustomisation": "enabled",
- "useScreenSharingCustomisation": "enabled",
- "useWebRTCAudioCustomisation": "enabled",
- "useWebRTCVideoCustomisation": "enabled",
- "instantMessagesCustomisation": "enabled",
- "userProfileCustomisation": "enabled",
- "fileStorageCustomisation": "enabled",
- "overridePresenceCustomisation": "enabled",
- "changeTelephonyCustomisation": "enabled",
- "changeSettingsCustomisation": "enabled",
- "recordingConversationCustomisation": "enabled",
- "useGifCustomisation": "enabled",
- "useDialOutCustomisation": "enabled",
- "fileCopyCustomisation": "enabled",
- "fileTransferCustomisation": "enabled",
- "forbidFileOwnerChangeCustomisation": "enabled",
- "readReceiptsCustomisation": "enabled",
- "useSpeakingTimeStatistics": "enabled",
- "useTeamsMode": "enabled",
- "userAvatarCustomisation": "enabled",
- "selectedAppCustomisationTemplate": null,
- "useRoomAsRBVoiceUser": "disabled",
- "useWebRTCAudioAsRBVoiceUser": "disabled",
- "canAccessWhatsNew": "enabled",
- "canAccessFaqCustomisation": "enabled",
- "canAccessHelpCenterCustomisation": "enabled",
- "canAccessStoreCustomisation": "disabled",
- "canDownloadAppCustomisation": "enabled",
- "canUseTestConfigCustomisation": "enabled",
- "canUseSendReportCustomisation": "enabled",
- "canUseTaskCustomisation": "enabled",
- "canSynchCalendar": "enabled",
- "canCallParticipantPbxNumberCustomisation": "enabled",
- "canSetInvisiblePresenceCustomisation": "enabled"
}, - "loggedInApplication": {
- "id": "08ad88a0028011e8bd1a8788ab975478",
- "name": "My application",
- "type": "web",
- "activity": "J",
- "ownerId": "573f189f774e0a428ee813a3",
- "dateOfCreation": "2018-05-04T14:12:41.413Z",
- "dateOfDeploymentRequest": "2018-06-18T07:22:16.530Z",
- "dateOfDeployment": "2018-06-18T07:22:16.530Z",
- "env": "deployed",
- "state": "active",
- "platform": "official"
}
}1 - Get an access code to realize a passwordless login
This API allows the user to get a once-time access code (OTP) to be used for passwordless login. This access code has then to be provided to the API POST /api/rainbow/authentication/v1.0/passwordless/login in order to proceed to the passwordless authentication and retrieve a JWT token.
This API is meant to be used by users configured to use passwordless authentication method:
- either they are configured to use their company's default authentication method (their setting
authenticationTypeis not set) and their company's default authentication method is arainbowPasswordlessPolicies(authentication setting havingenabledForAllCompanyUsersset to true) - either they are configured to use a given
rainbowPasswordlessPoliciesof their company (their settingauthenticationTypeis set toRAINBOWand theirrainbowPasswordlessPolicy.rainbowPasswordlessPolicyIdis set to one of their company'srainbowPasswordlessPolicies) The user must have the featureSECURITY_PASSWORDLESSin his profile.
Depending on their company's rainbowPasswordlessPolicies configured for the user:
- the code is sent by email and/or by SMS.
- the code length is between 6 and 10 digits,
- the code duration is between 60 seconds (1 minute) to 86400 seconds (24 hours)
The access code:
- can only be used once (it is revoked once the user authenticates with this code)
- is revoked if a new one is generated for the same uid
- is revoked once its expiration date is reached
A user can only request up to 5 codes per hour without success authentication. If the user requests a 6th code in less than 1 hour, an error 403538 is returned.
query Parameters
| uid required | string User unique identifier:
|
| country | string When the provided
Note that an error 400210 is returned in the case the provided |
header Parameters
| accept required | string application/json |
Responses
Response samples
- 200
- 400
- 500
{- "data": {
- "codeLength": 6,
- "codeDuration": 60,
- "expirationDate": "2024-04-12T08:22:40.148Z",
- "smsSent": true,
- "smsSentTo": "+*********89",
- "emailSent": false
}
}2 - Realize a passwordless login
This API allows Rainbow users to use a once-time access code (OTP) in order to login to Rainbow.
This API is meant to be used by users configured to use passwordless authentication method:
- either they are configured to use their company's default authentication method (their setting
authenticationTypeis not set) and their company's default authentication method is arainbowPasswordlessPolicies(authentication setting havingenabledForAllCompanyUsersset to true) - either they are configured to use a given
rainbowPasswordlessPoliciesof their company (their settingauthenticationTypeis set toRAINBOWand theirrainbowPasswordlessPolicy.rainbowPasswordlessPolicyIdis set to one of their company'srainbowPasswordlessPolicies) The user must have the featureSECURITY_PASSWORDLESSin his profile.
The access code to set in this API is obtained using with the API GET /api/rainbow/authentication/v1.0/passwordless/code.
The application is also authenticated during the user login.
If login is successful, the API returns a JSON Web Token (<abbr title="JSON Web Token">JWT) which has to be provided by clients for all Rainbow APIs requiring user authentication:
- The JWT is valid only for a given time period.
- The JWT can be renewed a few times using API GET /api/rainbow/authentication/v1.0/renew.
- The maximum number of renew is given in the JWT payload, as well as the current number of time the token has been renewed (see below).
- Once the JWT expired, or if the maximum of token renew has been reached, user must login again using this API.
The JWT returned contains the following data in payload:
{
"countRenewed": 0, // Number of times the token has been renewed
"maxTokenRenew": 5, // Number of times the token can be renewed
"user": {
"id": "572756967bfbca0d0e09a6b4", // Logged in user id
"loginEmail": "user@company.com" // Logged in user loginEmail
},
"app": {
"id": "598983029db9b5b14693a6f0", // Application id used for the authentication
"name": "My App" // Application name
},
"iat": 1463588327, // (Issued At) Time at which the JWT was issued
"exp": 2183588327 // (Expiration Time) Expiration time after which the JWT won't be accepted
}
If the uid / code combination is wrong, an error 401 is return (errorDetailsCode 401610).
If the appId / appSecret combination is wrong, an error 401 is return (errorDetailsCode 401500).
The following login protection is implemented:
- After 5 login failure, the user account is locked for 1 hour.
- As long as the maximum number of login failure has not been reached, a 401 error with errorDetailsCode
401610is returned. - Once the maximum number of login attempts has been reached, a 401 error with errorDetailsCode
401611is returned: the user account is locked for the given time period. - While the user account is locked, the same response with errorDetailsCode
401611will be returned for each new login attempt for this user account (even if a good uid / code combination is provided). If the uid / code combination is wrong, the locked time period restarts from this new wrong attempt. - Once the locked time period is over, a login with a valid uid / code combination will be allowed.
Request Body schema: application/json
| code required | string Passwordless code |
| uid required | string User unique identifier Must be the same uid than the one used to obtain the code (see API GET /api/rainbow/authentication/v1.0/passwordless/code) |
Responses
Request samples
- Payload
{- "code": "string",
- "uid": "string"
}Response samples
- 200
- 400
- 401
- 403
- 500
{- "token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1c2VyIjp7ImlkIjoiNTZjNWMxOWY5NDE0MTc2NTExOWY4OTZjIiwibG9naW5FbWFpbCI6InVzZXIxQGNvbXBhbnkuY29tIn0sImlhdCI6MTQ1NjE1MTYzOCwiZXhwIjoxNDU2MTU4ODM4fQ.FlPLNcWY9pTr0QvMj3RpLZJxtqbbydNnWIEr-B2lc4Y6ea41bqJJ-e10Sk_S-1blnG71E7yT625qrkO-UCc0ywR6lWCylcAUkH7-fvjKQbET2mU-4yuNwTd-sNHGzGabgr4n5xtUSMaDunjDgF1kQDZ-dEFPF5NtbN1rdqZP9tzTXrpZ6rmrW2a1o13-hHl7sxN_FqHr_4u_8AhN4dMKUgG0qRjrc1GMJ88M8idH9zTsejU5YQyJqdYQS9T_fSoFzJtS0rmwNCJMdeF2tXj8YQeTjKAiPXoBwklm5xblHxWeCTz9tqfkw1XeNxSO0pOUmpwdpF8kbwDCCa2rgz1z3A",
- "mfaRequired": false,
- "loggedInUser": {
- "id": "56c5c19f94141765119f896c",
- "loginEmail": "user1@company.com",
- "loginPhone": {
- "isValidated": true,
- "E164": "+33312345678",
- "national": "0312345678",
- "nationalWithoutPrefix": "312345678",
- "E164WithoutPrefix": "33312345678",
- "E164WithNationalPrefix": "+330312345678",
- "E164WithNationalPrefixWithoutPrefix": "330312345678"
}, - "firstName": "Firstname",
- "lastName": "Lastname",
- "displayName": "Firstname Lastname",
- "nickName": "Nickname",
- "title": "Mr.",
- "jobTitle": "Research and Development",
- "emails": [
- {
- "email": "user1@company.com",
- "type": "work"
}, - {
- "email": "user1@home.com",
- "type": "home"
}
], - "phoneNumbers": [
- {
- "shortNumber": "1002",
- "pbxId": "PBX712e-bd96-0c27-4350-a3ff-dc0c-83e7-c246",
- "systemId": "57dc0644f44a97c9155cd462",
- "country": "FRA",
- "number": "0390676767",
- "numberE164": "+33390676767",
- "phoneNumberId": "58876dad81e063e01187dd24",
- "isMonitored": true,
- "isFromSystem": true,
- "deviceType": "landline",
- "type": "work"
}, - {
- "number": "0390909090",
- "country": "FRA",
- "numberE164": "+33390909090",
- "phoneNumberId": "577e2e9b86c953de7838d635",
- "systemId": null,
- "isFromSystem": false,
- "deviceType": "landline",
- "type": "home"
}, - {
- "number": "0690909090",
- "country": "FRA",
- "numberE164": "+33690909090",
- "phoneNumberId": "577e2e9b86c953de7838d636",
- "systemId": null,
- "isFromSystem": false,
- "deviceType": "mobile",
- "type": "home"
}
], - "country": "FRA",
- "language": "fr-FR",
- "timezone": "Europe/Paris",
- "jid_im": "2d2f1aaf5ce54a2dbae9d70490366562@openrainbow.com",
- "jid_tel": "tel_2d2f1aaf5ce54a2dbae9d70490366562@openrainbow.com",
- "jid_password": "3b3f6e2c927940b2875f1ec604c0363b",
- "roles": [
- "user",
- "superadmin"
], - "adminType": "undefined",
- "companyId": "569ce8c8f9336c471b98eda1",
- "companyName": "My company",
- "isInDefaultCompany": false,
- "organisationId": null,
- "siteId": null,
- "visibility": "same_than_company",
- "isActive": true,
- "isInitialized": true,
- "initializationDate": "2016-01-18T13:30:44.498Z",
- "activationDate": "2016-01-18T13:29:44.498Z",
- "creationDate": "2016-01-18T12:45:44.498Z",
- "lastUpdateDate": "2016-01-19T16:33:22.548Z",
- "lastAvatarUpdateDate": "2016-01-19T11:29:11.567Z",
- "createdBySelfRegister": true,
- "createdByAdmin": {
- "userId": "56d69d020c92b35b3041d433",
- "loginEmail": "superadmin@localhost.fr"
}, - "invitedBy": {
- "invitationId": "574ffe07170a86f3297bc35b",
- "invitationDate": "2016-01-15T13:29:44.498Z",
- "userId": "56d69d020c92b35b3041d533",
- "loginEmail": "user0@company.com"
}, - "firstLoginDate": "2016-01-18T13:29:44.498Z",
- "lastLoginDate": "2016-02-23T09:17:42.523Z",
- "loggedSince": "2016-02-23T09:17:42.523Z",
- "isTerminated": false,
- "guestMode": false,
- "profiles": [
- {
- "isDefault": true,
- "status": "active",
- "canBeSold": false,
- "businessModel": "none",
- "businessSpecific": [
- "NONE"
], - "isExclusive": false,
- "isPrepaid": false,
- "hasConference": false,
- "isBundle": false,
- "assignationDate": "2017-02-17T13:35:27.427Z",
- "provisioningNeeded": [ ],
- "subscriptionId": "5808da2e35d795966e61f9ce",
- "offerId": "58079ed2041fa586e92337cd",
- "offerName": "Essential",
- "profileId": "580777f56fbd22a442d4fb57",
- "profileName": "Essential",
- "offerReference": "RB-Essential",
- "offerDescription": "Rainbow Essential offer",
- "offerTechnicalDescription": "Essential"
}
], - "customData": {
- "key1ANumber": 123,
- "key2AString": "a string",
- "key3ABoolean": true,
- "key4AnObject": {
- "myKey": "My value"
}
}, - "fileSharingCustomisation": "enabled",
- "userTitleNameCustomisation": "enabled",
- "softphoneOnlyCustomisation": "disabled",
- "useRoomCustomisation": "enabled",
- "phoneMeetingCustomisation": "enabled",
- "useChannelCustomisation": "enabled",
- "useScreenSharingCustomisation": "enabled",
- "useWebRTCAudioCustomisation": "enabled",
- "useWebRTCVideoCustomisation": "enabled",
- "instantMessagesCustomisation": "enabled",
- "userProfileCustomisation": "enabled",
- "fileStorageCustomisation": "enabled",
- "overridePresenceCustomisation": "enabled",
- "changeTelephonyCustomisation": "enabled",
- "changeSettingsCustomisation": "enabled",
- "recordingConversationCustomisation": "enabled",
- "useGifCustomisation": "enabled",
- "useDialOutCustomisation": "enabled",
- "fileCopyCustomisation": "enabled",
- "fileTransferCustomisation": "enabled",
- "forbidFileOwnerChangeCustomisation": "enabled",
- "readReceiptsCustomisation": "enabled",
- "useSpeakingTimeStatistics": "enabled",
- "useTeamsMode": "enabled",
- "userAvatarCustomisation": "enabled",
- "selectedAppCustomisationTemplate": null,
- "useRoomAsRBVoiceUser": "disabled",
- "useWebRTCAudioAsRBVoiceUser": "disabled",
- "canAccessWhatsNew": "enabled",
- "canAccessFaqCustomisation": "enabled",
- "canAccessHelpCenterCustomisation": "enabled",
- "canAccessStoreCustomisation": "disabled",
- "canDownloadAppCustomisation": "enabled",
- "canUseTestConfigCustomisation": "enabled",
- "canUseSendReportCustomisation": "enabled",
- "canUseTaskCustomisation": "enabled",
- "canSynchCalendar": "enabled",
- "canCallParticipantPbxNumberCustomisation": "enabled",
- "canSetInvisiblePresenceCustomisation": "enabled"
}, - "loggedInApplication": {
- "id": "08ad88a0028011e8bd1a8788ab975478",
- "name": "My application",
- "type": "web",
- "activity": "J",
- "ownerId": "573f189f774e0a428ee813a3",
- "dateOfCreation": "2018-05-04T14:12:41.413Z",
- "dateOfDeploymentRequest": "2018-06-18T07:22:16.530Z",
- "dateOfDeployment": "2018-06-18T07:22:16.530Z",
- "env": "deployed",
- "state": "active",
- "platform": "official"
}
}Initiate an OIDC authentication
This API allows Rainbow users to login using OpenID Connect (OIDC) authentication (using authorization code grant) if this type of authentication is provided by their company.
Authorization code grant is recommended as it is more secure than Implicit grant (it involves a clientSecret from Rainbow application). This API is dedicated to Authorization code grant, the OIDC flow being completely handled by Rainbow authentication server.
In order to use this API, the OIDC SingleSignOn settings of the company must contain:
clientId: the client_id for the Rainbow application created on the company's OIDC provider,clientSecret: the client_secret for the Rainbow application created on the company's OIDC provider,issuer: the company's OIDC provider issuer (should has been got from discoveryUrl if OIDC settings has been configured with this parameter).authorizationEndpoint: the company's OIDC provider authorization endpoint (should has been got from discoveryUrl if OIDC settings has been configured with this parameter).tokenEndpoint: the company's OIDC provider token endpoint (should has been got from discoveryUrl if OIDC settings has been configured with this parameter).jwksUri: the company's OIDC provider jwks_uri endpoint (should has been got from discoveryUrl if OIDC settings has been configured with this parameter).
The full OIDC flow using Authorization Code grant is detailed in the following sequence diagram.
This GET /api/rainbow/authentication/v1.0/oidc-client/login endpoint addresses points 3 to 7 of this diagram
(point 2 is addressed by GET /api/rainbow/authentication/v1.0/urls?uid=user@company.com endpoint, see related documentation).
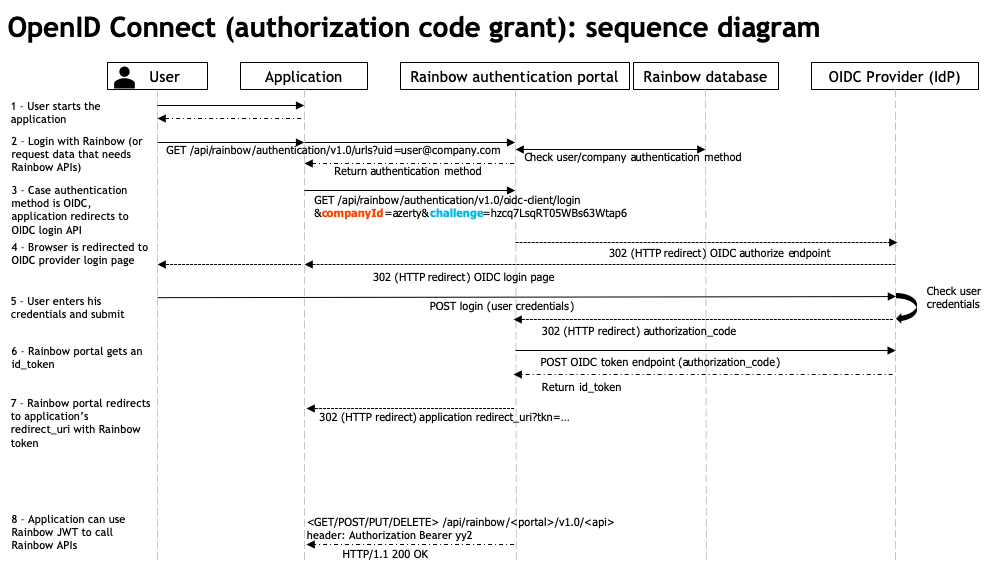
Details about the sequence diagram:
- (1) User starts application
- (2) Application requests Rainbow Authentication portal’s API GET /api/rainbow/authentication/v1.0/urls?uid=user@company.com
to know what is the authentication type to use for this user. - (3) In the case the authentication type is OIDC for this user, the application has to redirect the browser / open a web view to this URL.
x-rainbow-app-authfield has to be provided in query parameters to authenticate the application (sha256 hash is computed using the challenge)
- Rainbow Authentication portal implements the OIDC authorization code grant flow:
- (4) Rainbow Authentication portal redirects the browser to the OIDC server’s authorize endpoint,
- (5) user enter his credentials in the OIDC server’s login page,
- (6) OIDC server send an authorization_code to a redirect_uri on Rainbow Authentication portal,
- (6) Rainbow Authentication portal calls OIDC server’s token endpoint to exchange this authorization_code against an id_token,
- (6) Rainbow Authentication portal decodes the id_token, looks for a Rainbow user with this email as loginEmail,
finds the OIDC SSO setting of his company and validates the id_token (validation of id_token signature, id_token expiration, issuer and audience fields).
- (7) Rainbow Authentication portal generates a Rainbow JWT and redirects the browser to the application’s
ssoAuthenticationRedirectUrl (default to Official Rainbow web client) with this jwt in query string (tkn query parameter). - (8) Rainbow JWT can be use to call Rainbow APIs
In the case errors occur during the OIDC client login flow, the browser is redirected to the application’s ssoAuthenticationRedirectUrl (default to Official Rainbow web client) with the following query parameters:
errtype: always set to OIDC for errors returned by this API,errcode: an error detailed code associated to the error (ex: 401500)errmsg: an error message code associated to the error (ex: Unknown application or wrong token for application id 204583b32039df11e9a07425538fb36c74)
query Parameters
| companyId required | string User company identifier This value is automatically set in the loginUrl which can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com |
| singleSignOnId required | string User company's SingleSignOn setting identifier This value is automatically set in the loginUrl which can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com |
| loginHint | string User login hint This value is automatically set in the loginUrl which can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com
in the case the |
| uiLocales | string User preferred languages When supported by the OIDC provider, As stated by OIDC RFC: This value is automatically set in the loginUrl which can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com
in the case the
Note that the |
| challenge required | string Challenge for application authentication This value can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com |
| x-rainbow-app-auth required | string Application authentication It has to be computed as follow: <base64encode(appId:sha256(appSecretchallenge))> (concatenation of appSecret and challenge, hashed with sha256). The challenge used to compute the |
| x-rainbow-client-version | string The client version In the case the parameter x-rainbow-client-version could not be provided in the headers, it can be provided in the query string parameters. The client version is used to verify if the client application has the minimal version required to use the Rainbow servers infrastructure. If the version of the client is under the configured minimal version, the login is refused and an error 403 is returned (403020). The minimal version required is set by the Rainbow infrastructure team when needed (for example, when some breaking changes has been added on server side, when a security issue has been identified on client side, ...). Client version example: 1.75.0 |
| backchannelSessionId | string Backchannel session identifier, allowing client application to perform the SSO authentication flow in the user's browser (i.e. outside the application) and getting the authenticated user's JWT from a polling API. This value is automatically set in the loginUrl which can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com
in the case the client requests to use backchannel polling and the |
| useBackchannelAuthenticationRedirectUrl | boolean Allows client application to perform the SSO authentication flow in the user's browser (i.e. outside the application) and to get the authenticated user's JWT from the backchannelAuthenticationRedirectUrl set in application's configuration (the browser is redirected to this URL at the end of the OIDC authentication flow with user's JWT set in tkn query parameter).
|
header Parameters
| x-rainbow-client-version | string The client version The client version is used to verify if the client application has the minimal version required to use the Rainbow servers infrastructure. If the version of the client is under the configured minimal version, the login is refused and an error 403 is returned (403020). The minimal version required is set by the Rainbow infrastructure team when needed (for example, when some breaking changes has been added on server side, when a security issue has been identified on client side, ...). Client version example: 1.75.0 |
Responses
Response samples
- 200
{- "tkn": "string"
}Initiate an SAML authentication
This API allows Rainbow users to login using SAML authentication if this type of authentication is provided by their company.
query Parameters
| companyId required | string User company identifier This value is automatically set in the loginUrl which can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com |
| challenge required | string Challenge for application authentication This value can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com |
| x-rainbow-app-auth required | string Application authentication It has to be computed as follow: <base64encode(appId:sha256(appSecretchallenge))> (concatenation of appSecret and challenge, hashed with sha256). The challenge used to compute the |
| x-rainbow-client-version | string The client version The client version is used to verify if the client application has the minimal version required to use the Rainbow servers infrastructure. If the version of the client is under the configured minimal version, the login is refused and an error 403 is returned (403020). The minimal version required is set by the Rainbow infrastructure team when needed (for example, when some breaking changes has been added on server side, when a security issue has been identified on client side, ...). Client version example: 1.75.0 |
| backchannelSessionId | string Backchannel session identifier, allowing client application to perform the SSO authentication flow in the user's browser (i.e. outside the application) and getting the authenticated user's JWT from a polling API. This value is automatically set in the loginUrl which can be retrieved using GET /api/rainbow/authentication/v1.0/urls?uid=user1@company.com
in the case the client requests to use backchannel polling and the |
| useBackchannelAuthenticationRedirectUrl | boolean Allows client application to perform the SSO authentication flow in the user's browser (i.e. outside the application) and to get the authenticated user's JWT from the backchannelAuthenticationRedirectUrl set in application's configuration (the browser is redirected to this URL at the end of the SAML authentication flow with user's JWT set in tkn query parameter).
|
Responses
Response samples
- 302
- 400
- 403
- 404
- 500
- 503
{- "None": { }
}1 - OAuth Authorization Request
This endpoints allows applications to get authorization from Rainbow users to use Rainbow APIs with their account. This delegation of access can be performed using OAuth 2.0 Authorization code grant or Implicit grant.
While both OAuth 2.0 Authorization Code grant and Implicit grant are supported by Rainbow, Authorization Code grant is recommended as it is more secure.
Implicit grant is recommended for browser applications implemented in JavaScript that can't provide a backend server handling the token exchange flow of OAuth Authorization Code grant. Indeed, such applications should not embed appSecret in their source code for security reasons, and Implicit grant allow them to retrieve the OAuth access token without sending the appSecret to Rainbow server (redirect_uri is the only security available with this flow). The limitation of implicit grant is that only an access token is returned, which has a limited lifetime and can't be renewed. Application has to execute again the whole Implicit grant flow to retrieve a new access token.
To enable Implicit grant for an application, the application's setting enableOAuthImplicitGrant has to
be set to true (it is disabled by default).
For more information, see the OAuth 2.0 RFC related to authorization endpoint:
- section 4.1.1 for Authorization Code grant,
- section 4.2.1 for Implicit grant.
Note that Rainbow applications are named client in OAuth 2.0 RFC.
1. Authorize request for Authorization code grant
The OAuth Authorization Code Grant flow is detailed in the following sequence diagram.
This GET /api/rainbow/authentication/v1.0/oauth/authorize endpoint addresses points 1 to 7 of this diagram for Authorization code grant flow
(points 8 to 9 are addressed by POST /api/rainbow/authentication/v1.0/oauth/token endpoint).
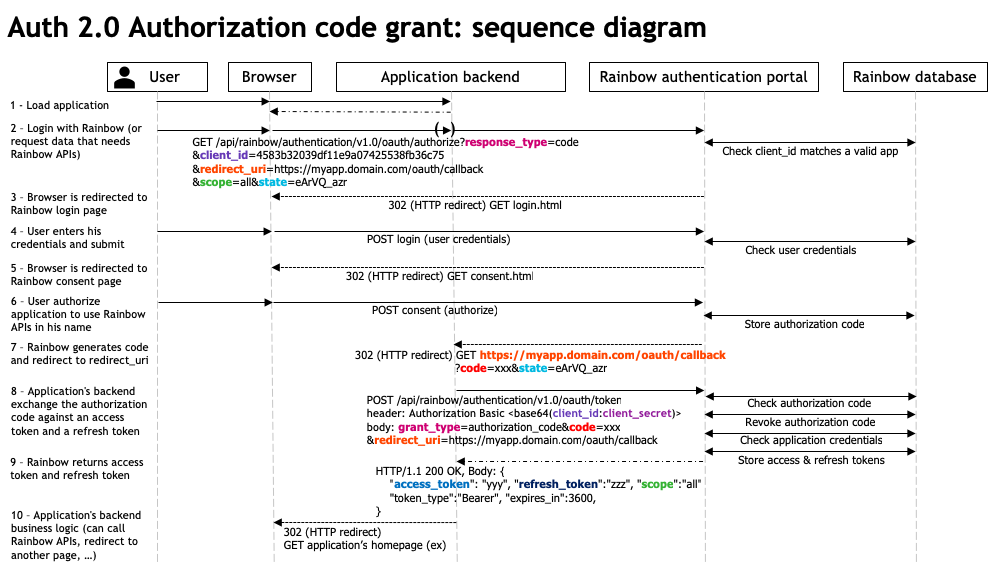
Details about the sequence diagram:
(1) User is on application website
(1) User accesses to application content that needs data from Rainbow, or application allows to login with Rainbow,
… (use case depends of the application needs)
(2) Application redirects to OAuth authorize endpoint on Rainbow authentication server.
Some query string parameters are provided in the query (defined by OAuth 2.0 RFC):
response_type: "code" for requesting an authorization code (authorization code grant)client_id: the application identifier (appId)redirect_uri: application's backend endpoint where the authorization code will be sent.
It has to use TLS for security reasons, as the authorization code is exchanged between Rainbow and the application's backend through the browser.scope: scope of the access requested by the application.
Currently, only "all" is supported (meaning that the application will have full access on all the Rainbow APIs).
In a next step, scopes will be defined so that the application can request restricted scopes (filestorage, bubble management, channels, …)state: a "random" value sent by the client to maintain a state between the request and the callback. Can be used to protect against cross-site request forgery attacks (CSRF).
(3) Rainbow authentication server checks that the
client_idsent in query parameter in (2) corresponds to a valid application in the database.- If so, Rainbow authentication server redirects user's browser to Rainbow login page
- Otherwise, an error is returned (if redirect_uri is provided, user's browser is redirected to this uri and the error is sent in query parameters)
(4) User enters his credentials on login page and submit the form. Rainbow authentication server checks in the database if user credentials are valid.
- If user credentials are incorrect, Rainbow authentication server redirects again user's browser to login page with an error which is displayed for the user.
- If user credentials are valid, Rainbow authentication server checks if the user authentication requires a 2nd factor (MFA).
- If 2nd factor is required, user's browser is redirected to mfa page.
User enters his 2nd factor and submit the form. Rainbow authentication server checks if user's 2nd factor is valid. Note: user can also enter his recovery code (if recovery code is valid, user authentication is granted and MFA is disabled for this user).- If user's 2nd factor is incorrect, Rainbow authentication server redirects again user's browser to mfa page with an error which is displayed for the user
- If 2nd factor is required, user's browser is redirected to mfa page.
(5) Rainbow authentication server redirects user's browser to consent page (except if app's setting disableOAuthConsentScreen is true, in this case step (6) is skipped).
(6) User authorize the application to access Rainbow APIs in his name. The form is submitted on Rainbow authentication server.
(7) If the user authorized, Rainbow authentication server generates an authorization code and redirects user's browser to application backend's
redirect_uri(the one provided in query parameters in (2)).Note that
redirect_urimust be one of the configuredoauthRedirectUrisin the application, otherwise an error is returned.The following data are returned in query parameters of the redirection uri (defined by OAuth 2.0 RFC):
code: the authorization code that can be exchanged against an access token and a refresh token using token endpoint. Authorization code has a short lifetime (10 minutes) and can only be used once.state: if state was provided in (2), this value is returned (otherwise a random value is returned).
If the user declined, Rainbow authentication server redirects user's browser to application backend's
redirect_uriwith an error in query parameters.
Once the application has the authorization code, it has to exchange it against an access token and a refresh token using POST /api/rainbow/authentication/v1.0/oauth/token endpoint, points 8 and 9 of the sequence diagram (see documentation of this endpoint for more information).
2. Authorize request for Implicit grant
The OAuth Implicit Grant flow is detailed in the following sequence diagram.
Unlike Authorization Code grant flow, this GET /api/rainbow/authentication/v1.0/oauth/authorize endpoint is the only one to be used by the application to retrieve the OAuth access token.
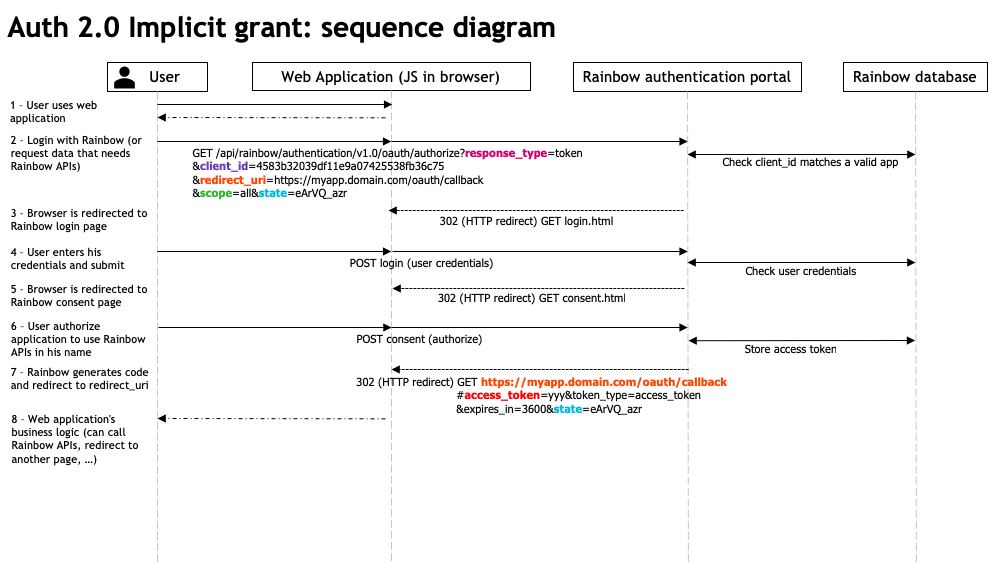
Details about the sequence diagram:
(1) User uses the web application on his browser
(1) User accesses to web application content that needs data from Rainbow, or web application allows to login with Rainbow, … (use case depends of the application needs)
(2) Application redirects to OAuth authorize endpoint on Rainbow authentication server.
Some query string parameters are provided in the query (defined by OAuth 2.0 RFC):
response_type: "token" for requesting an access token (implicit grant)client_id: the application identifier (appId)redirect_uri: web application's endpoint where the authorization code will be sent.scope: scope of the access requested by the application.
Currently, only "all" is supported (meaning that the application will have full access on all the Rainbow APIs).
In a next step, scopes will be defined so that the application can request restricted scopes (filestorage, bubble management, channels, …)state: a "random" value sent by the client to maintain a state between the request and the callback. Can be used to protect against cross-site request forgery attacks (CSRF).
(3) Rainbow authentication server checks that the
client_idsent in query parameter in (2) corresponds to a valid application in the database.- If so, Rainbow authentication server redirects user's browser to Rainbow login page
- Otherwise, an error is returned (if redirect_uri is provided, user's browser is redirected to this uri and the error is sent in fragment component of this redirection uri)
(4) User enters his credentials on login page and submit the form. Rainbow authentication server checks in the database if user credentials are valid.
- (5) If so, Rainbow authentication server redirects user's browser to consent page
- Otherwise, Rainbow authentication server redirects again user's browser to login page with an error which is displayed for the user
(6) User authorize the application to access Rainbow APIs in his name. The form is submitted on Rainbow authentication server.
(7) If the user authorized, Rainbow authentication server generates an access token and redirects user's browser to web application's
redirect_uri(the one provided in query parameters in (2)).Note that
redirect_urimust be one of the configuredoauthRedirectUrisin the application, otherwise an error is returned.The following data are returned in fragment component of the redirection uri (defined by OAuth 2.0 RFC):
access_token: the access token that can be used by the application to use Rainbow APIs,token_type: the type of token returned ("access_token"),expires_in: the lifetime of the access token (in seconds),state: if state was provided in (2), this value is returned (otherwise a random value is returned).
If the user declined, Rainbow authentication server redirects user's browser to application's
redirect_uriwith an error in fragment component.
Once the application has the access token, it can use it to use Rainbow APIs with the account of the related Rainbow user.
query Parameters
| response_type required | string Desired grant type to use for authorize endpoint.
For more information, details are available in the OAuth 2.0 RFC, section 3.1.1 and section 4.1.1 (Authorization Code grant) or section 4.2.1 (Implicit grant). |
| client_id required | string Unique identifier of the application requesting the authorization
(also documented as For more information, details are available in the OAuth 2.0 RFC, section 2.2 and section 4.1.1 (Authorization Code grant) or section 4.2.1 (Implicit grant). |
| redirect_uri | string Application's endpoint URI where the user-agent will be redirected with the authorization code (Authorization Code grant) or access token (Implicit grant) if the user grants access to the application. Errors are redirected to this endpoint as well, for example in the case the user declines access to the application. If If If Authorization Code grant is used, this endpoint should use TLS for security reasons, as sensitive data are sent to application's endpoint through a public network. For more information, details are available in the OAuth 2.0 RFC, section 3.1.2 and section 4.1.1 (Authorization Code grant) or section 4.2.1 (Implicit grant). |
| scope | string The scope of the Rainbow API access requested by the application. For now, only For more information, details are available in the OAuth 2.0 RFC, section 3.3 and section 4.1.1 (Authorization Code grant) or section 4.2.1 (Implicit grant). |
| state | string A random string that can be provided by the application to maintain state between the authorize request and the redirection to redirect_uri endpoint (state is sent back by Rainbow authentication server to redirect_uri endpoint). This should be used by the application to prevent against cross-site request forgery (CSRF). For more information, details are available in the OAuth 2.0 RFC, section 4.1.1. For more information regarding cross-site request forgery (CSRF) threat, details are available in the section 10.12. |
| x-rainbow-client-version | string The client version The client version is used to verify if the client application has the minimal version required to use the Rainbow servers infrastructure. If the version of the client is under the configured minimal version, the login is refused and an error 403 is returned (403020). The minimal version required is set by the Rainbow infrastructure team when needed (for example, when some breaking changes has been added on server side, when a security issue has been identified on client side, ...). Client version example: 1.75.0 |
header Parameters
| content-type required | string application/x-www-form-urlencoded |
Responses
Response samples
- 200
{- "access_token": "string",
- "code": "string",
- "expires_in": 0,
- "state": "string",
- "token_type": "string"
}2 - OAuth Access Token Request
This endpoints allows applications to get an access token allowing them to use Rainbow APIs with the account of the related Rainbow user.
Access token has a short lifetime (1 hour). A refresh token is issued as well, allowing applications to refresh their access token (and such avoiding the application to request user authorization again with GET /api/rainbow/authentication/v1.0/oauth/authorize).
The token endpoint can be used:
- To exchange the authorization code against an access token and a refresh token,
- To get a new access token using the refresh token (to be used when the access token has expired).
1. Exchange the authorization code against an access token and a refresh token
For more information, see the OAuth 2.0 RFC, section 4.1.3 related to the use of this endpoint to exchange the authorization code against an access token and a refresh token.
The OAuth Access Token Request flow is detailed in the following sequence diagram.
This POST /api/rainbow/authentication/v1.0/oauth/token endpoint addresses points 8 to 9 of this diagram
(points 1 to 7 are addressed by GET /api/rainbow/authentication/v1.0/oauth/authorize endpoint).

Details about the sequence diagram:
(8) application's backend exchanges the authorization code it retrieved in (7) against an access token and a refresh token.
For that, it calls the OAuth token endpoint on Rainbow authentication server. It has to provide:
The header Authorization with Basic <base64encode(
client_id:client_secret)>.This request has to be done from the application''s backend so that the client_secret (appSecret) remains confidential.
Example of base64 calculation:
base64("78e98ee09bad11e8b8edebb50d679df6:2UrOcs3agk34zaV3Jsf01vM54iLyqwBEpnv5vJr72D9cE5wMVQeEe3BM7IxzyyJD") = <i>NzhlOThlZTA5YmFkMTFlOGI4ZWRlYmI1MGQ2NzlkZjY6MlVyT2NzM2FnazM0emFWM0pzZjAxdk01NGlMeXF3QkVwbnY1dkpyNzJEOWNFNXdNVlFlRWUzQk03SXh6eXlKRA==</i>
In the body the parameters (x-www-form-urlencoded):
grant_type: must be set to "authorization_code" for an exchange of an authorization code against an access token and a refresh tokencode: the authorization code sent by Rainbow authentication server in (7)redirect_uri: the redirect_uri parameter, must be the same than the one used to retrieve the authorization code (the one sent in (2))- (9) Rainbow authentication server checks that the application's credentials are valid by extracting client_id and client_secret from the Authorization header and comparing them to the appId and appSecret stored in the database. Then it checks that the provided authorization code is valid, has well been generated for this application and redirect_uri matches the one sent in (2). Provided authorization code is revoked, as it can only be used once.
- If everything is valid, Rainbow authentication server generates an access token and a refresh token that it stores in the database and returns in the body of the HTTP response to the application's backend.
- Otherwise, a body with an error message is returned to the application's backend.
- (10) With the access token received from the Rainbow authentication server in (9), the application can use it to call Rainbow APIs in the name of the user.
For that, it calls the Rainbow APIs with the header Authorization Bearer
.
2. Refresh an access token
Access token has a short lifetime (1 hour). If the application tries to use an expired access token for a request on Rainbow API, an error 401 Unauthorized is returned. Access token can be renewed using the refresh token, this avoids the application to redo the whole OAuth authorization code flow.
For more information, see the OAuth 2.0 RFC, section 6 related to the refresh of an access token.
The OAuth Refresh Access Token flow is detailed in the following sequence diagram.
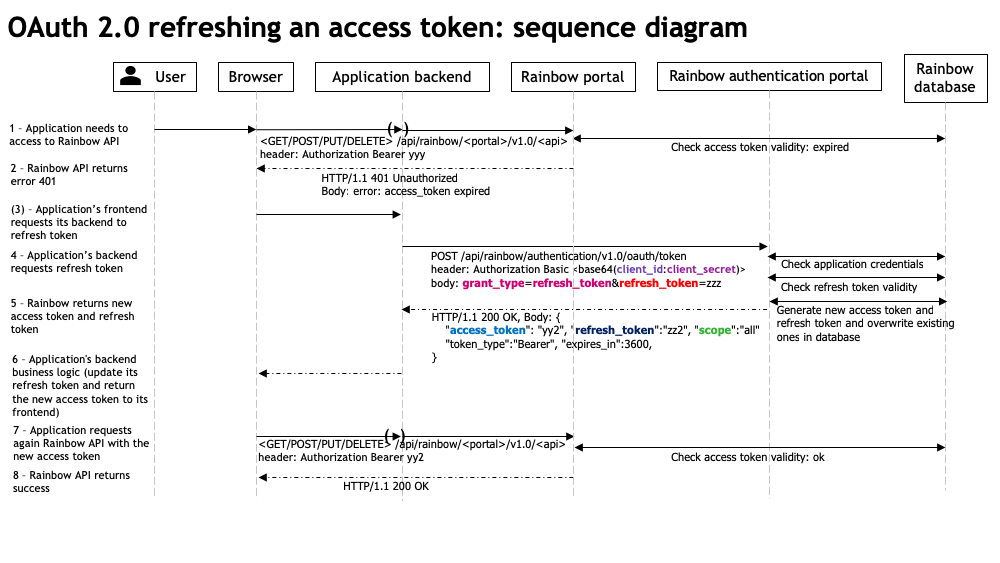 Details about the sequence diagram:
Details about the sequence diagram:
(1) User is on application website
(1) User accesses to application content that needs data from Rainbow (use case depends of the application needs).
The application has already an OAuth access token and a refresh token retrieved using the authorization code grant described in "OAuth Authorization Code Grant sequence diagram".
(1) Application calls the Rainbow API (whatever the portal is) to access Rainbow user data. It provides the header
Authorization: Bearer <access_token>in the request.(2) Rainbow API portal checks the validity of the access token (existing, not expired).
(2) If the access token is expired, an error 401 Unauthorized is returned. The application needs to renew the access token.
(3) [optional, depends of the application implementation] If the application is executed in the browser (JavaScript), it needs to request its backend to get a new access token.
If the request to Rainbow API is already performed in the application's backend, the backend itself can renew the access token.
(4) Application's backend calls the OAuth token endpoint on Rainbow authentication server. It has to provide:
- The header Authorization with Basic <base64(
client_id:client_secret)>. This request has to be done from the application's backend so that the client_secret (appSecret) remains confidential.
- The header Authorization with Basic <base64(
Example of base64 calculation: base64("78e98ee09bad11e8b8edebb50d679df6:2UrOcs3agk34zaV3Jsf01vM54iLyqwBEpnv5vJr72D9cE5wMVQeEe3BM7IxzyyJD") =
<i>NzhlOThlZTA5YmFkMTFlOGI4ZWRlYmI1MGQ2NzlkZjY6MlVyT2NzM2FnazM0emFWM0pzZjAxdk01NGlMeXF3QkVwbnY1dkpyNzJEOWNFNXdNVlFlRWUzQk03SXh6eXlKRA==</i>In the body the parameters (x-www-form-urlencoded)
grant_type: must be set to "refresh_token" to request a new access token using the refresh tokenrefresh_token: the refresh token sent by Rainbow authentication server- (5) Rainbow authentication server checks that the client credentials are valid by extracting client_id and client_secret from the Authorization header and comparing them to the appId and appSecret stored in the database. Then it checks that the provided refresh token is valid, not expired, and has well been generated for this application.
- If everything is valid, Rainbow authentication server generates a new access token and returns both access token and refresh token in the body of the HTTP response to the application's backend.
If theenableOAuthRefreshTokenRotationsetting is enabled for this application (it is enabled by default), a new refresh token is also generated and this new one is returned in the body of the HTTP response. The current refresh token is then revoked. - Otherwise, a body with an error message is returned to the application's backend.
- (6) The application updates its access token and refresh token in its own storage.
In the case the application is running in the browser, the backend returns the new access token to its frontend.
- (7) The application redo the same API request to Rainbow portal done in (1), with the newly generated access token.
- (8) Rainbow API portal checks the validity of the access token. As the access token is now valid, the Rainbow API performs the requested operation / returns the requested data.
Request Body schema: application/json
| code | string The authorization code sent by Rainbow authentication server from the GET /api/rainbow/authentication/v1.0/oauth/authorize endpoint. Mandatory to exchange an authorization code against an access token. Note that once it has been used, the authorization code is revoked. For more information, details are available in the OAuth 2.0 RFC, section 4.1.3. |
| grant_type required | string Enum: "authorization_code" "refresh_token" Desired grant type to use for token endpoint. Must be set to:
|
| redirect_uri | string The redirect_uri used to retrieve the authorization code sent by Rainbow authentication server from the GET /api/rainbow/authentication/v1.0/oauth/authorize endpoint. Mandatory to exchange an authorization code against an access token. For more information, details are available in the OAuth 2.0 RFC, section 4.1.3. |
| refresh_token | string The refresh token sent by Rainbow authentication server from the GET /api/rainbow/authentication/v1.0/oauth/authorize endpoint of from a previous refresh token performed using this POST /api/rainbow/authentication/v1.0/oauth/token endpoint. Mandatory to refresh an access token. The provided refresh_token must not be expired. If the refresh token is expired, the application has to redo the whole OAuth authorization code flow. Note that once it has been used to refresh an access token, the refresh_token is revoked. The new refresh token returned in the response with the access token replaces the previous one. For more information, details are available in the OAuth 2.0 RFC, section 6. |
Responses
Request samples
- Payload
{- "code": "string",
- "grant_type": "authorization_code",
- "redirect_uri": "string",
- "refresh_token": "string"
}Response samples
- 200
{- "access_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1c2VyIjp7ImlkIjoiNTcyNzU2OTY3YmZiY2EwZDBlMDlhNmI0In0sImFwcCI6eyJpZCI6Ijc4ZTk4ZWUwOWJhZDExZThiOGVkZWJiNTBkNjc5ZGY2IiwibmFtZSI6IkFwcF9SYWluYm93XzEifSwib2F1dGgiOnsidHlwZSI6ImFjY2Vzc190b2tlbiIsInNjb3BlIjoiYWxsIn0sImlhdCI6MTU1MzUyMDE2NH0.pKyIDJWWk6N3Ee0slCF2tZNGzGmX5xpzPAgYaDQ93pohVjpHaOdAgIDE0LEK68DudQSIZnUUi3DklpbrS75tQBRJX95e-zYiQTa2fARBVPxwwOnx3PROtVh1eJvZrBsJK3MiPi-mQCGL8RZICJux1_igKy7f_Bhl7hdswJ7gZMW1WSqRYJWD93Fdlchj-qrquO0dKxzkfJMDjKyQzVCGEb8ChUvtTO7QFKeyhgHfP5nXEgkDd4LPMr9hjfJ1rqtEl3sbWJvo6DWuRZqTd3AvWgIKgprtQePC8QEtdpl-1LBBhrAI_y0RNs0u67ODKXQjZPdIBM07XnVAAD6JrHGGhg",
- "expires_in": 3600,
- "token_type": "Bearer",
- "refresh_token": "eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJ1c2VyIjp7ImlkIjoiNTcyNzU2OTY3YmZiY2EwZDBlMDlhNmI0In0sImFwcCI6eyJpZCI6Ijc4ZTk4ZWUwOWJhZDExZThiOGVkZWJiNTBkNjc5ZGY2IiwibmFtZSI6IkFwcF9SYWluYm93XzEifSwib2F1dGgiOnsidHlwZSI6InJlZnJlc2hfdG9rZW4iLCJzY29wZSI6ImFsbCJ9LCJpYXQiOjE1NTM1MjAxNjR9.hauDetfLAglWLiBTwPg8ArCSolAN4S9BIjl_vJ5D5mNpduPWEvDjjcuiRSfVYg9rNmowSSlhk2ISDPvqPkViuLlGeYbaBdPqea4NZCYI1mK-wwJcDw1VyT4f2JagNJaAI-vmadxj9en2MLjXekGSAIQ79cObElJI0L8vezEPPcloupvMLmFzCTCThRNZuEM1aaTF4-Ov-lEy3DrDOpNigPwXpT0JA4GtN4w7GTXCu2YAC0RswA8y3x_uwWx7IHe76haW2b22V6euwYQ2zd2Wb8Hq2aSz7afGKGWgWXJycotlZz9ZSwx4NkDT4XY_Nqy2wZgijcgqq21xq9S5E7puOQ",
- "scope": "all"
}